Transport Layer Security 1.3 (RFC 8446)
1. Major differences from TLS 1.2
- All legacy algorithms have been deprecated. TLS 1.3 uses AEAD instead.
- 0-RTT (zero round-trip time) mode was added.
- All public-key based key exchange mechanisms now provide forward secrecy.
- Simplified the handshake state machine (removed ChangeCipherSpec in most common cases).
- Cryptographic improvements.
- KDF: HMAC-based KDF
- RSA padding
- DSA removed
- Ephemeral Diffie-Hellman removed
- Session resumption has beed replaced by a simple PSK exchange
AEAD: Authenticated Encryption with Associated Data
2. Protocal Overview
Handshake Protocal and Record Protocal
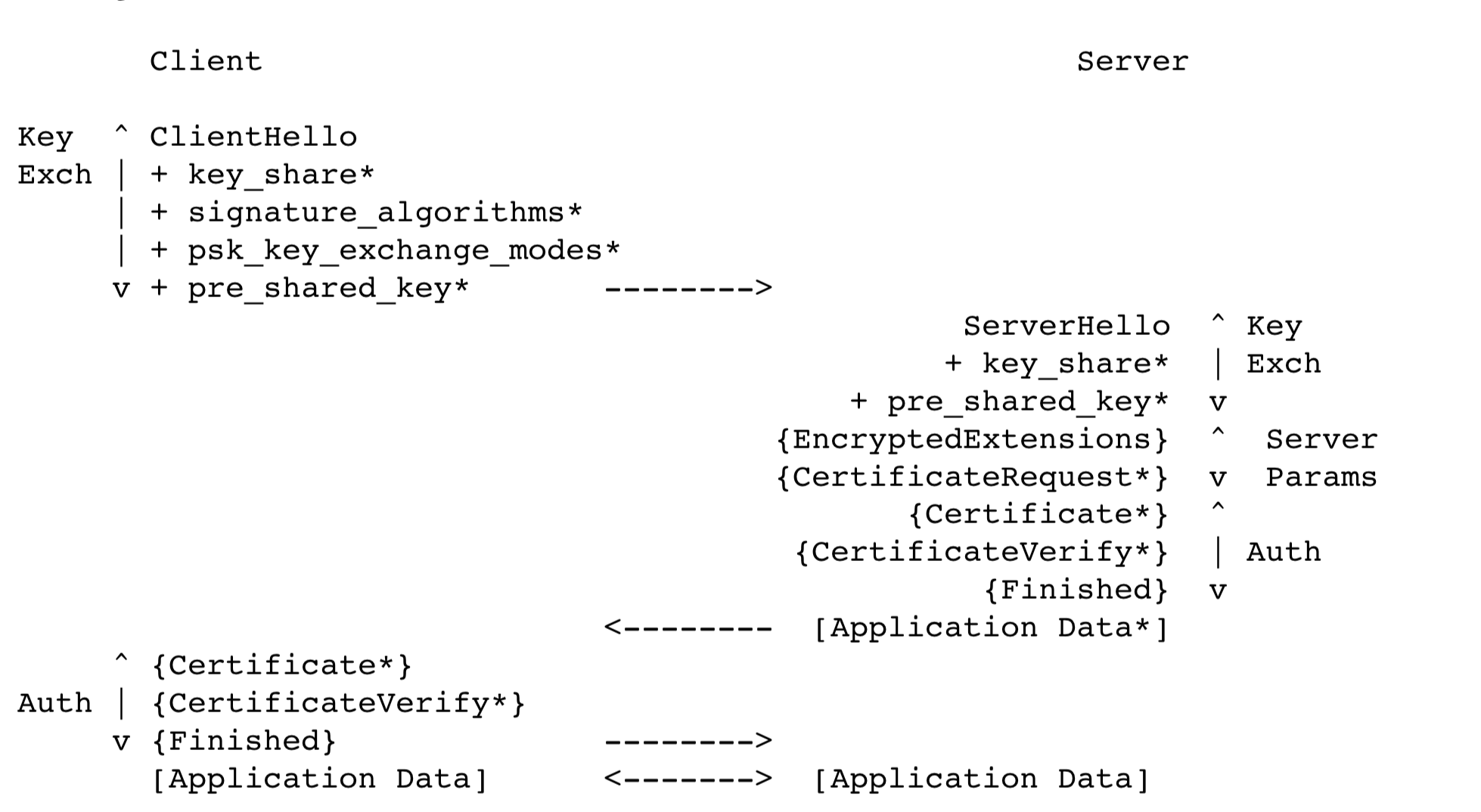
Basic Key Exchange Modes:
- (EC)DHE (Diffie-Hellman over either finite fields or elliptic curves)
- PSK-only
- PSK with (EC)DHE
Session Resumption in TLS 1.3
Session ID used in TLS 1.2 has been obsoleted.
PSK: a PSK identity that corresponds to a unique key derived from the initial handshake.
In TLS 1.3:
- PSKs are used in ECDHE (with FS)
- PSKs are used alone (without FS)
0-RTT mode
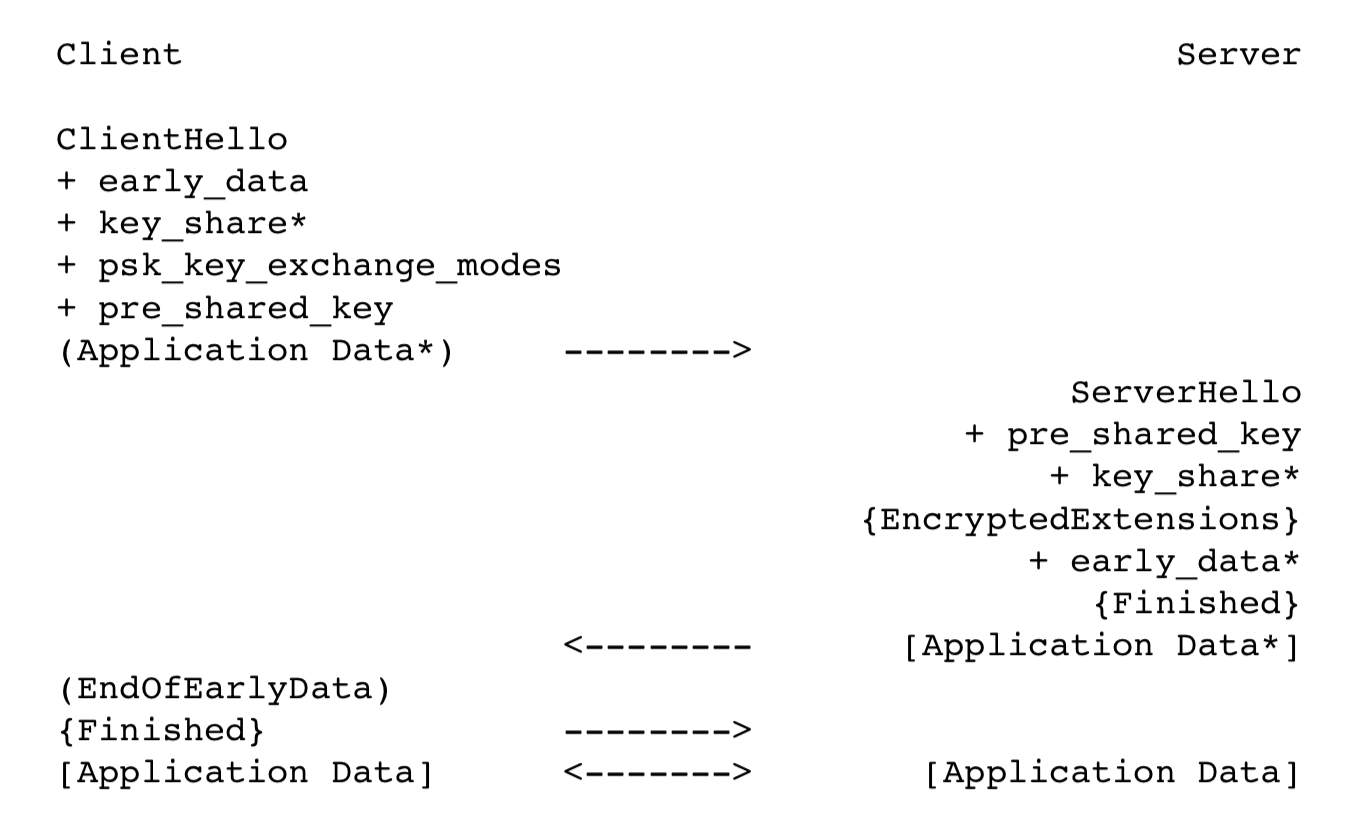
The security properties for 0-RTT data are weaker than those for other kinds of TLS data.
- no gurantees of forward security: used PSKs only
- no guarantees of non-replay
3. HandShake Protocal
No renegotiation in TLS 1.3
Three basic functions:
- Key Exchange Messages
- Server Parameters Messages
- Authentication
Client Hello: either a set of Diffie-Hellman key shares (in the “key_share” (Section 4.2.8) extension), a set of pre-shared key labels (in the “pre_shared_key” (Section 4.2.11) extension), or both;
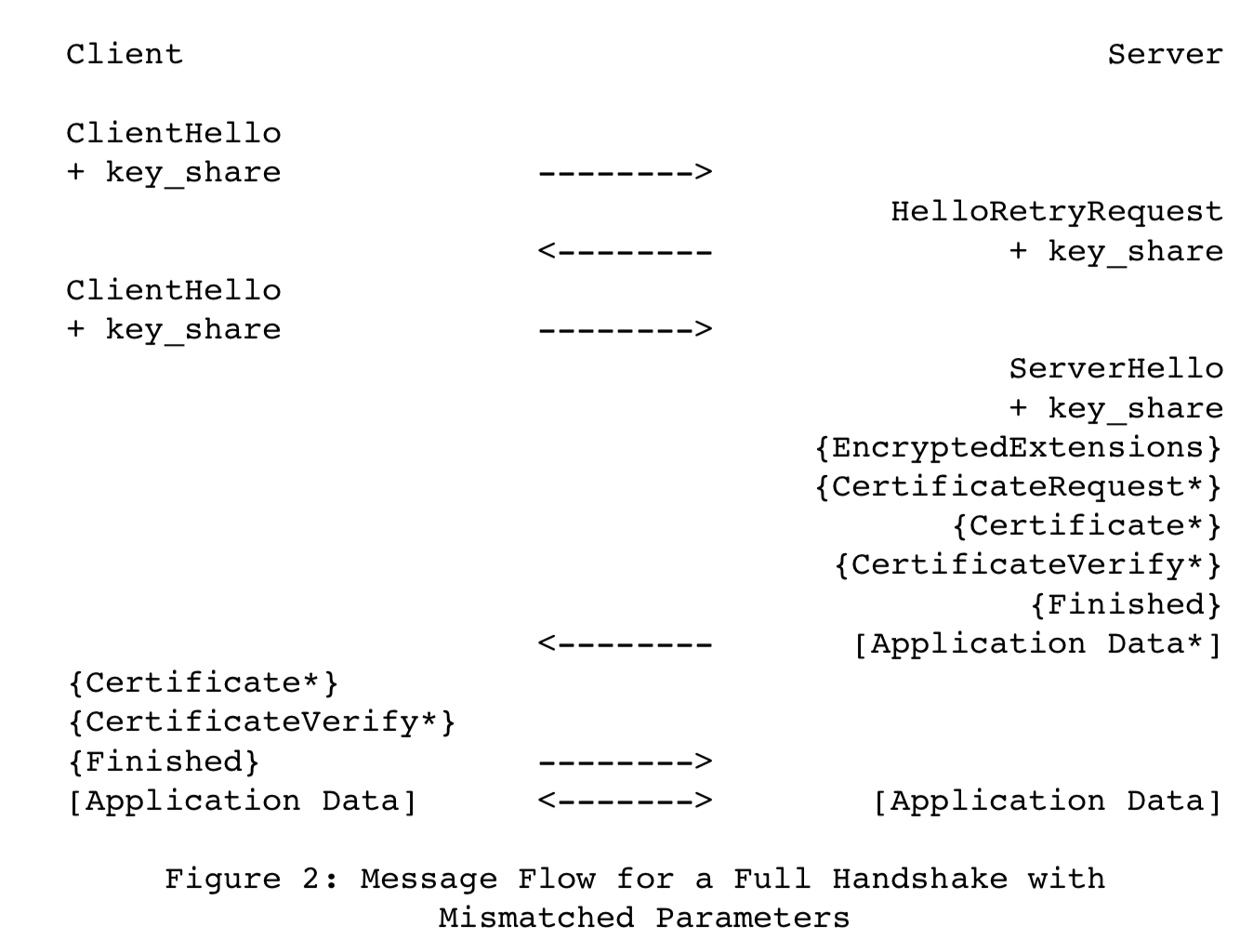
Incorrect DHE Share
the server corrects the mismatch with a HelloRetryRequest and the client needs to restart the handshake with an appropriate “key_share” extension
4. Record Protocal
Four types: handshake, application_data, alert, and change_cipher_spec.
change_cipher_spec is used only for compatibility purposes
Record Protocal may be encrypted by AEAD algorithms.( application_data)
5. 0-RTT and Anti-Replay
In order to defense the replay attack in 0-RTT, there are two baisc requirements:
- The server MUST ensure that any instance of it would accept 0-RTT for the same 0-RTT handshake at most once;
- Applications must anti-replay
How to do?
- Single-Use Tickets
- Client Hello Recording
- Freshness Checks
本人保留对侵权者及其全家发动因果律武器的权利
版权提醒
如无特殊申明,本站所有文章均是本人原创。转载请务必附上原文链接:https://www.elliot98.top/post/lab/rfc8446/。
如有其它需要,请邮件联系!版权所有,违者必究!
 Elliot's Blog
Elliot's Blog