Brief
- author: Emma Dauterman, Henry Corrigan-Gibbs, David Mazières, Dan Boneh, Dominic Rizzo
- From: Stanford and Google
Introduction
双因子认证是目前对抗弱密码等恶意攻击的有效手段。其中一种是使用 U2F 硬件认证。但是使用硬件也可能给系统带来新的安全隐患(后门等)。
由于 U2F 在分发过程中需要在服务器中记录 seed,一旦攻击装获取seed就可以恢复公私钥,进而破坏系统安全性。
使用主秘钥和会话秘钥分离也可能发生cache和 swap 攻击等。
U2F 认证过程
U2F 双因子认证设计三个对象:U2F 硬件、浏览器和可靠服务器。
协议要求
- 防止恶意的token
- 防止 compromised browser
- Protect against token fingerprinting.
- 对服务器端透明
- 不改变硬件条件
密码学技术
1. 数字签名
- Sig.KeyGen() → (sk, pk). Output a secret signing key sk and a public verification key pk.
- Sig.Sign(sk, m) → σ. Output a signature σ on the message m ∈ M using the secret key sk.
- Sig.Verify(pk, m, σ) → {0, 1}. Output “1” iff σ is a valid signature on message m under public key pk.
2. Verifiable random function (VRF)
- VRF.KeyGen() → (skVRF, pkVRF). Output a secret key and a public key.
- VRF.Eval(skVRF, id) → (y, π). Take as input the secret key skVRF, and an input id ∈ I, and output a value y ∈ Z∗q along with a proof π.
- VRF.Verify(pkVRF, id, y, π) → {0, 1}. Take as input the public ∗ keypkVRF,apurportedinput-outputpair(id,y)∈I×Zq,and a proof π. Return “1” iff π is a valid proof that (id, y) is an input-output pair.
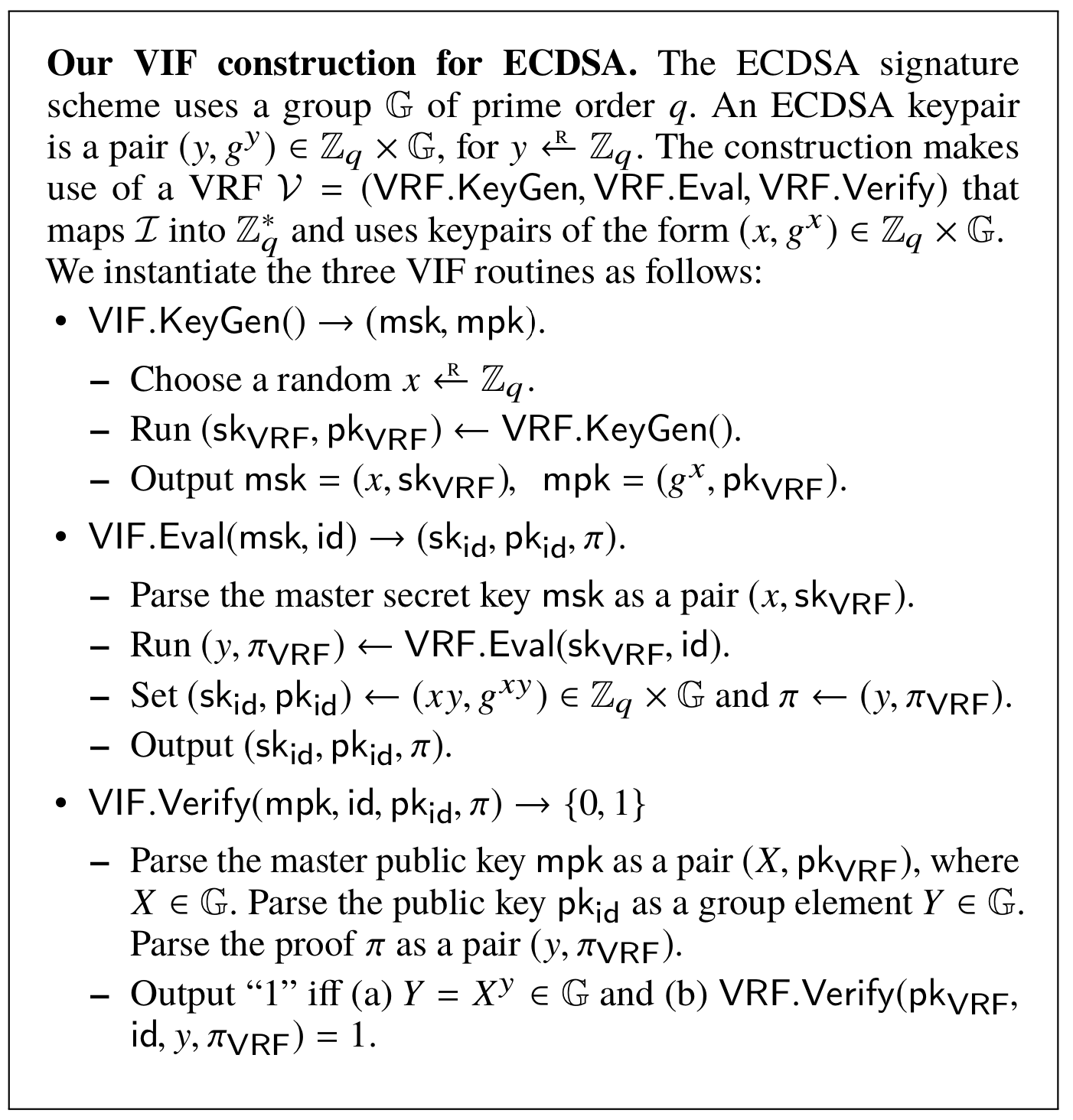
3. New tool: Verifiable identity families (VIFs)
作者在 VRF 的基础上加以修改,成为 VIFs
- VIF.KeyGen()→(msk,mpk).Outputamastersecretkeymsk and a master public key mpk.
- VIF.Eval(msk, id) → (skid, pkid, π). Given an identity string id ∈ I, output the keypair (skid, pkid) corresponding to that identity, as well as a proof π that pkid is well formed. The keypair (skid, pkid) must be a valid keypair for the signature scheme Σ.
- VIF.Verify(mpk, id, pkid, π) → {0, 1}. Verify that pkid is the public key for identity id ∈ I corresponding to master public key mpk using the proof π. Return “1” iff the proof is valid.
实现:
4. New tool: Fast collaborative key generation
需要为VIFs 生成秘钥对。需要保证正确性、无偏和零知识。
- The browser commits to a random value v ∈ Zq . That is, the browser samples v ←R Zq and r ←R Zq and sends c ← H(v, r) to the token.
- Thetokensamplesv′ ←R Zq andsendsV′ ←gv′ ∈Gtothe browser.
- The browser opens its commitment to v by sending (v, r ) to the token. The browser outputs X ← V ′ · gv ∈ G as the public key.
- The token checks that H(v, r) = c. If so, the token accepts and outputs x ← v + v′ ∈ Zq. Otherwise, the token outputs “⊥.” Completeness follows immediately.
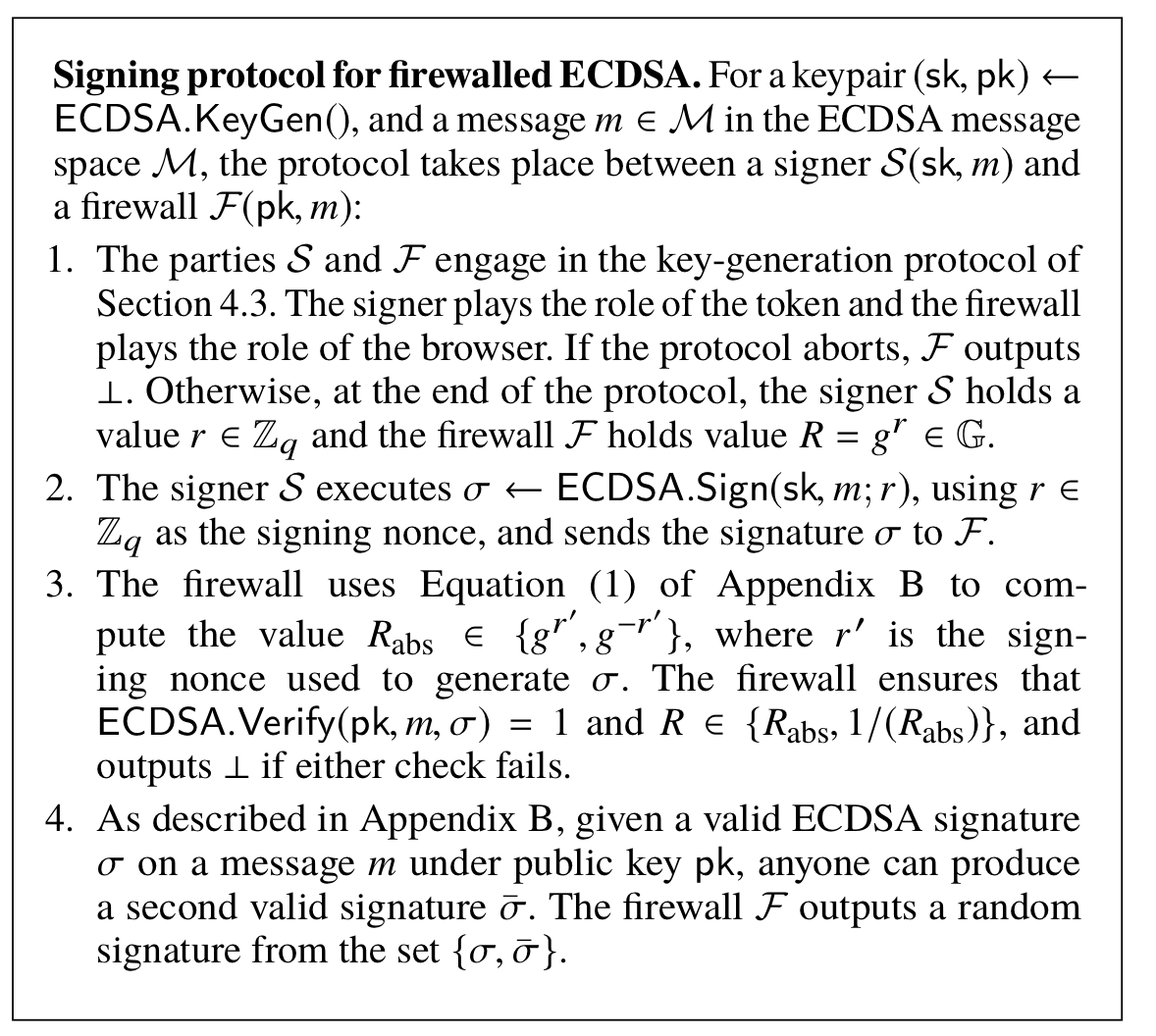
5. New tool: Firewalled ECDSA signatures
6. 计数算法
需要一个对小容量硬件友好的计数算法。值得注意的是需要对于flash做优化。
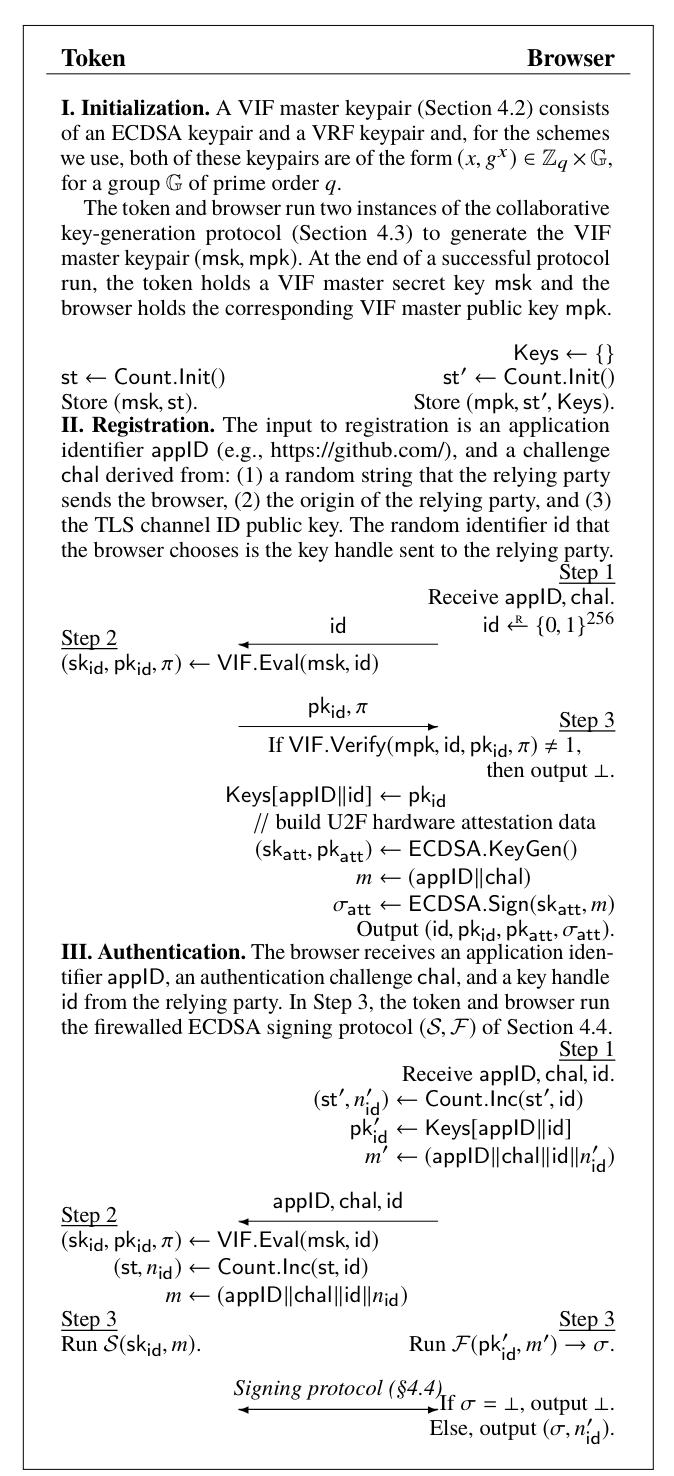
协议实现
本人保留对侵权者及其全家发动因果律武器的权利
版权提醒
如无特殊申明,本站所有文章均是本人原创。转载请务必附上原文链接:https://www.elliot98.top/post/lab/ps2019-3/。
如有其它需要,请邮件联系!版权所有,违者必究!
 Elliot's Blog
Elliot's Blog