maTLS: How to Make TLS middlebox-aware?
Hyunwoo Lee, Zach Smith, Junghwan Lim†, Gyeongjae Choi, Selin Chun, Taejoong Chung, Ted “Taekyoung” Kwon
Network and Distributed Systems Security (NDSS) Symposium 2019
Current Solution
MITM:
- Client: fake root certificate
- Server: CDNs request server private keys.
=> Increased risks in MITM attack
=> How to work honestly?
1. encryption-based
2. TEE-based
3. TLS extension-based
SplitTLS:
- authentication: client can not authenticate the intend server
- Confidentiality: weak ciphersuite
- Integrity:Not behaved Middlebox
maTLS:
- authenticate all middleboxes
- audit all middleboxes
- security parameter verification
- valid modification checks
Middlebox transparency (MT): MT system targets middlebox certificates, it logs certificates, which can be publicly mon- itored and audited by any interested parties.
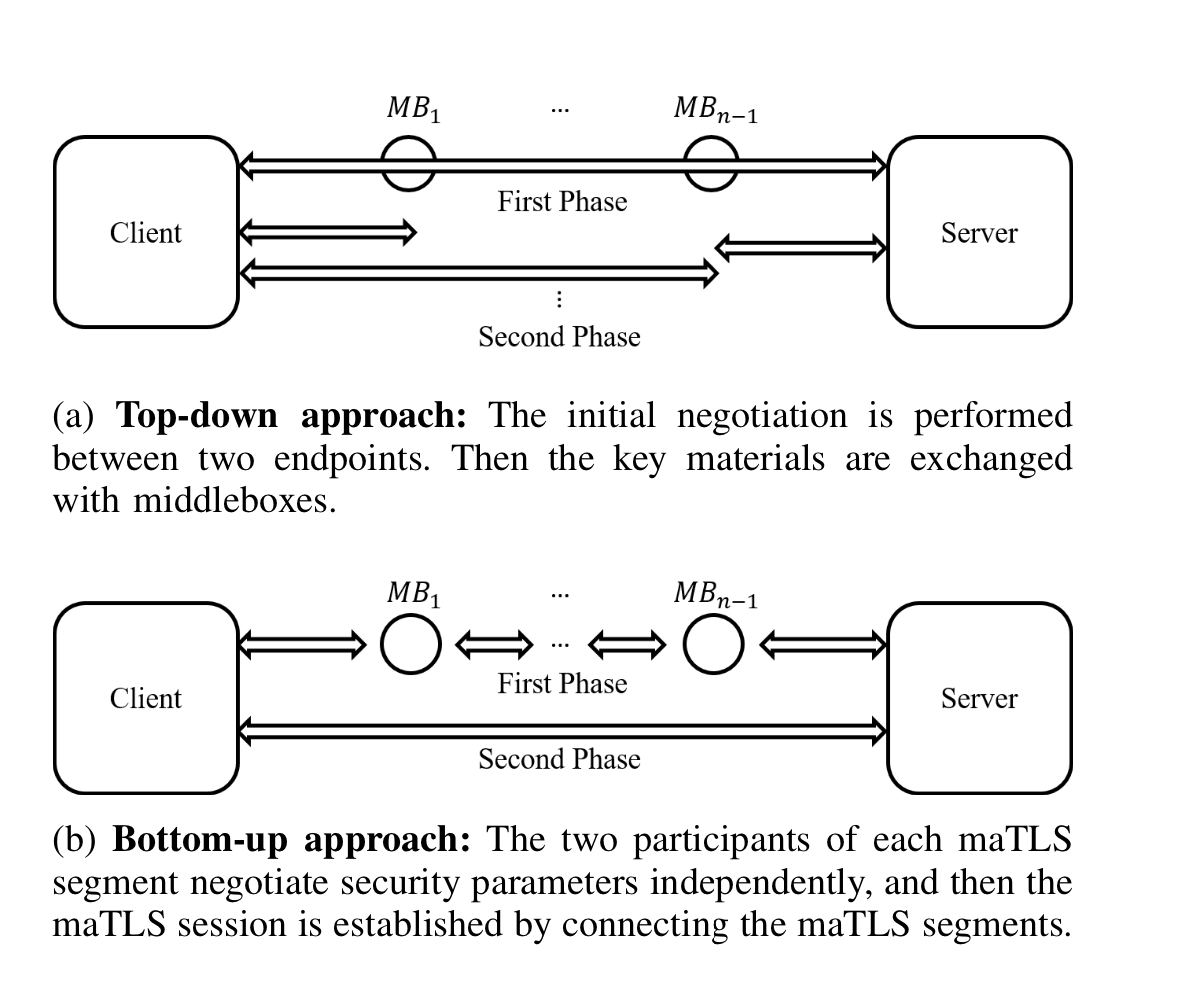
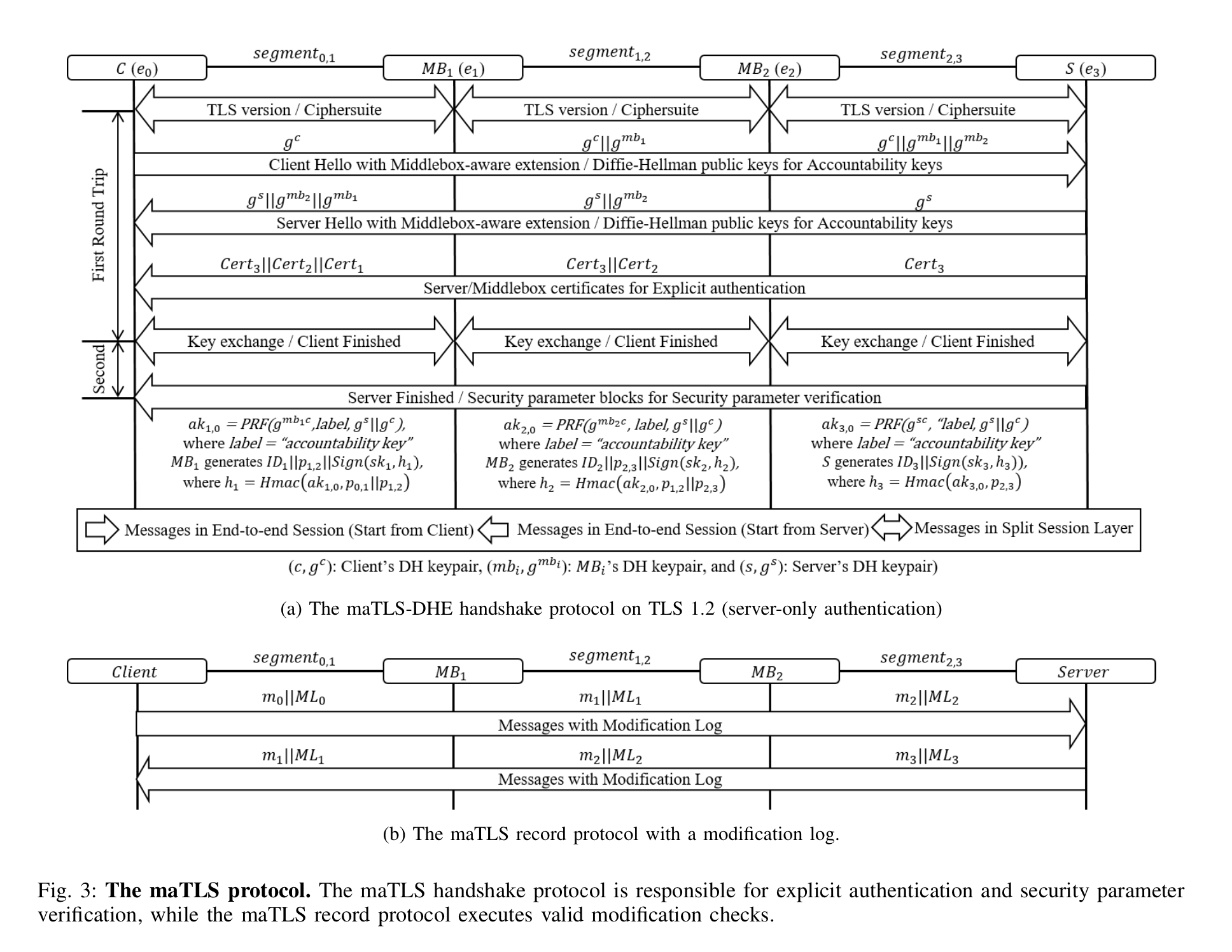
How to do
An extension in middlebox’ X509 Certificates indicates the access of this middlebox.
本人保留对侵权者及其全家发动因果律武器的权利
版权提醒
如无特殊申明,本站所有文章均是本人原创。转载请务必附上原文链接:https://www.elliot98.top/post/lab/ndss2019-matls/。
如有其它需要,请邮件联系!版权所有,违者必究!
 Elliot's Blog
Elliot's Blog